As an alternative communication system during disaster, LTE private networks adopt different security policies at multiple levels to prevent illegal users from accessing or stealing data, and to protect the security of user signaling and business data.
Physical Layer
●Adopt dedicated frequency bands to physically isolate the access of equipment with unlicensed frequency band.
●Users use IWAVE tactical lte solution mobile phones and UIM cards to prevent illegal device access.
Network Layer
●The Milenage algorithm and five-tuple authentication parameters are used to achieve two-way authentication between the UE and the network.
When a terminal accesses the network, the network will authenticate the terminal to prevent illegal users from accessing. At the same time, the terminal will also authenticate the network to prevent access to the phishing network.
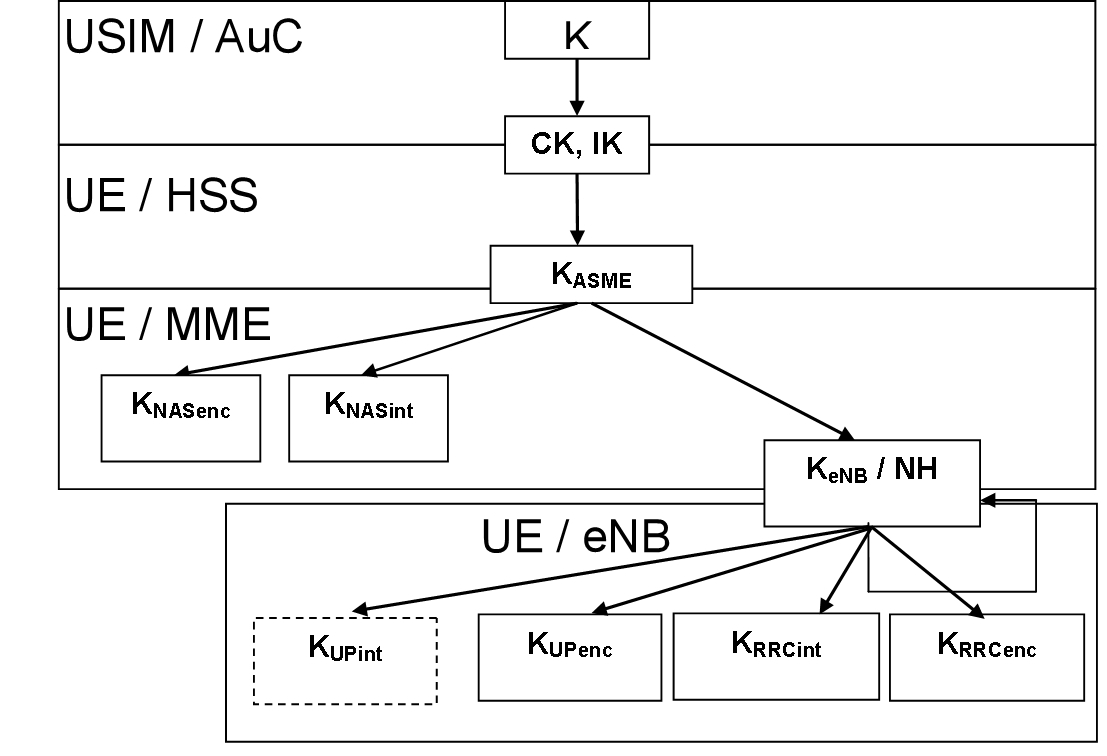
Figure 1: Key Generation Algorithm
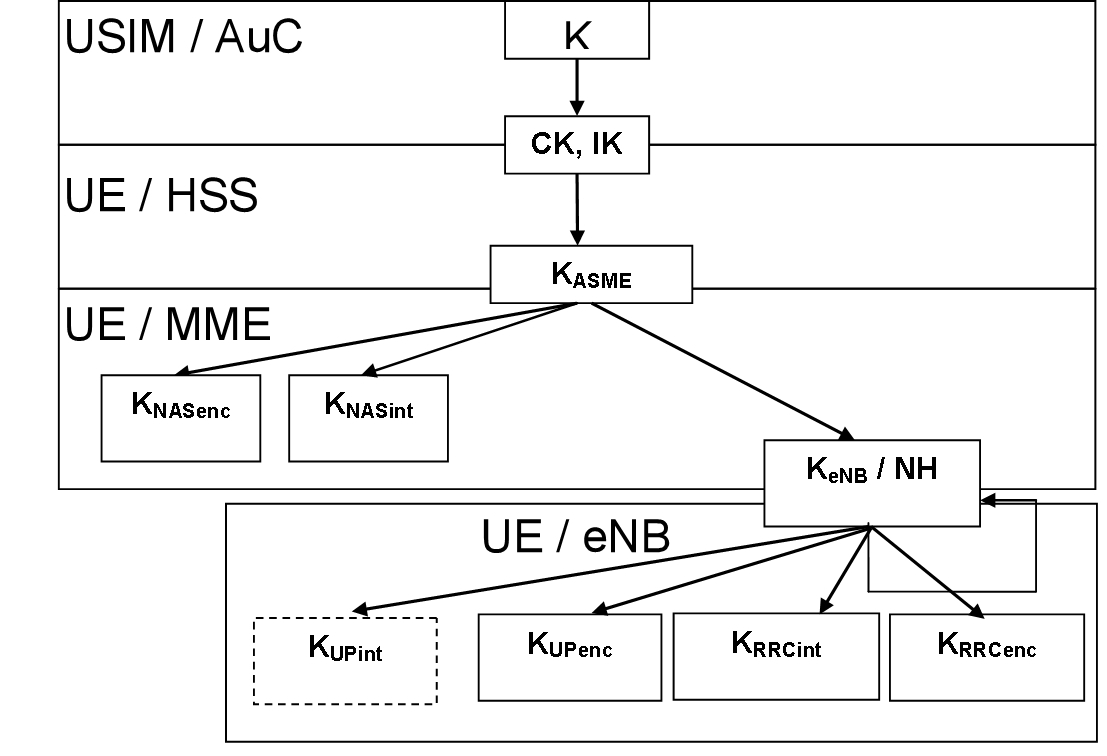
Figure 2: Dependencies of authentication parameters
●Air interface signaling messages support integrity protection and encryption, and data of user also supports encryption. The integrity and encryption protection algorithm uses a 128-bit length key and has high security strength. The below Figure 3 shows the generation process of authentication-related parameters, in which HSS and MME are both internal functional modules of the tactical lte network.
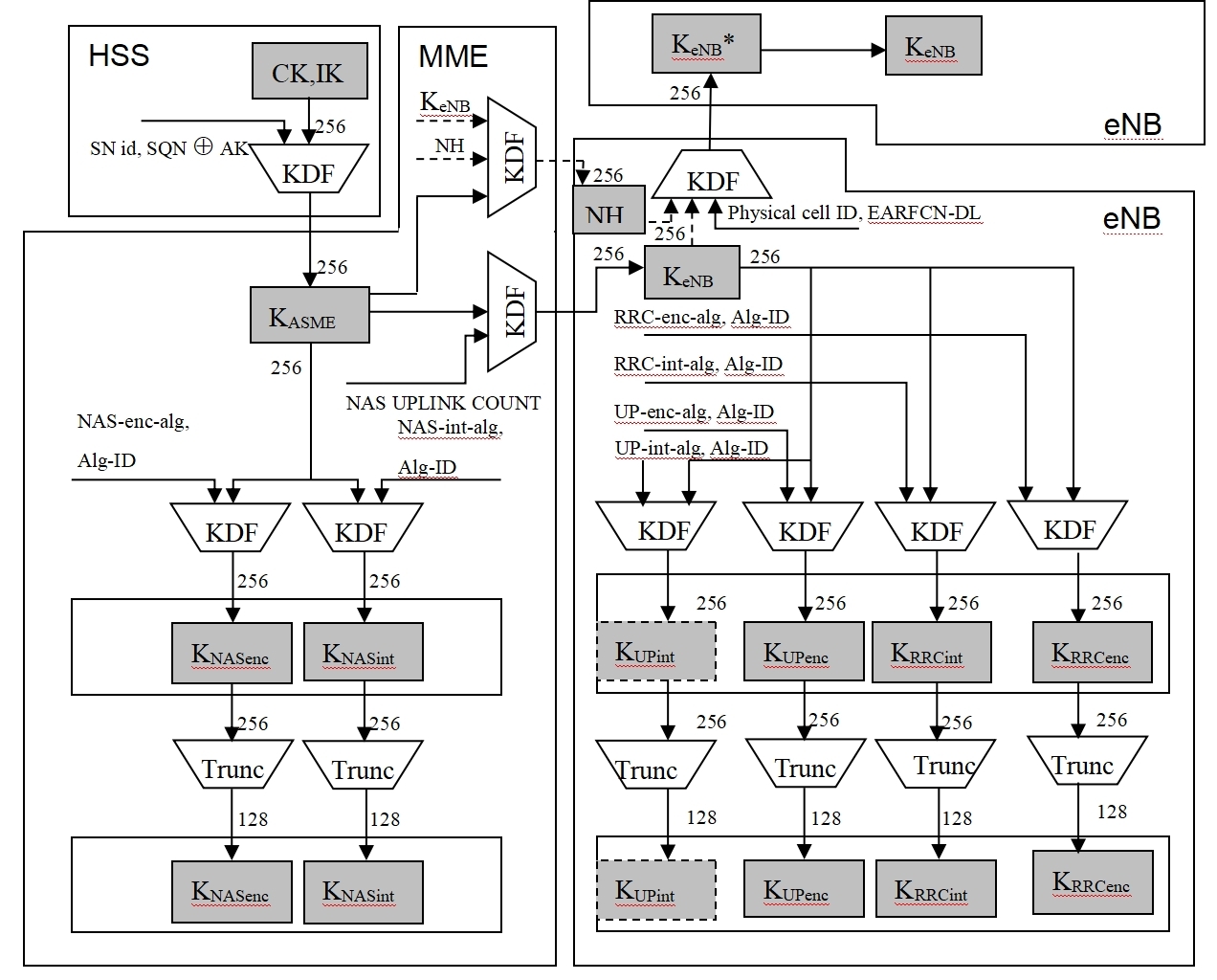
Figure 3: Generation process of private network authentication parameters
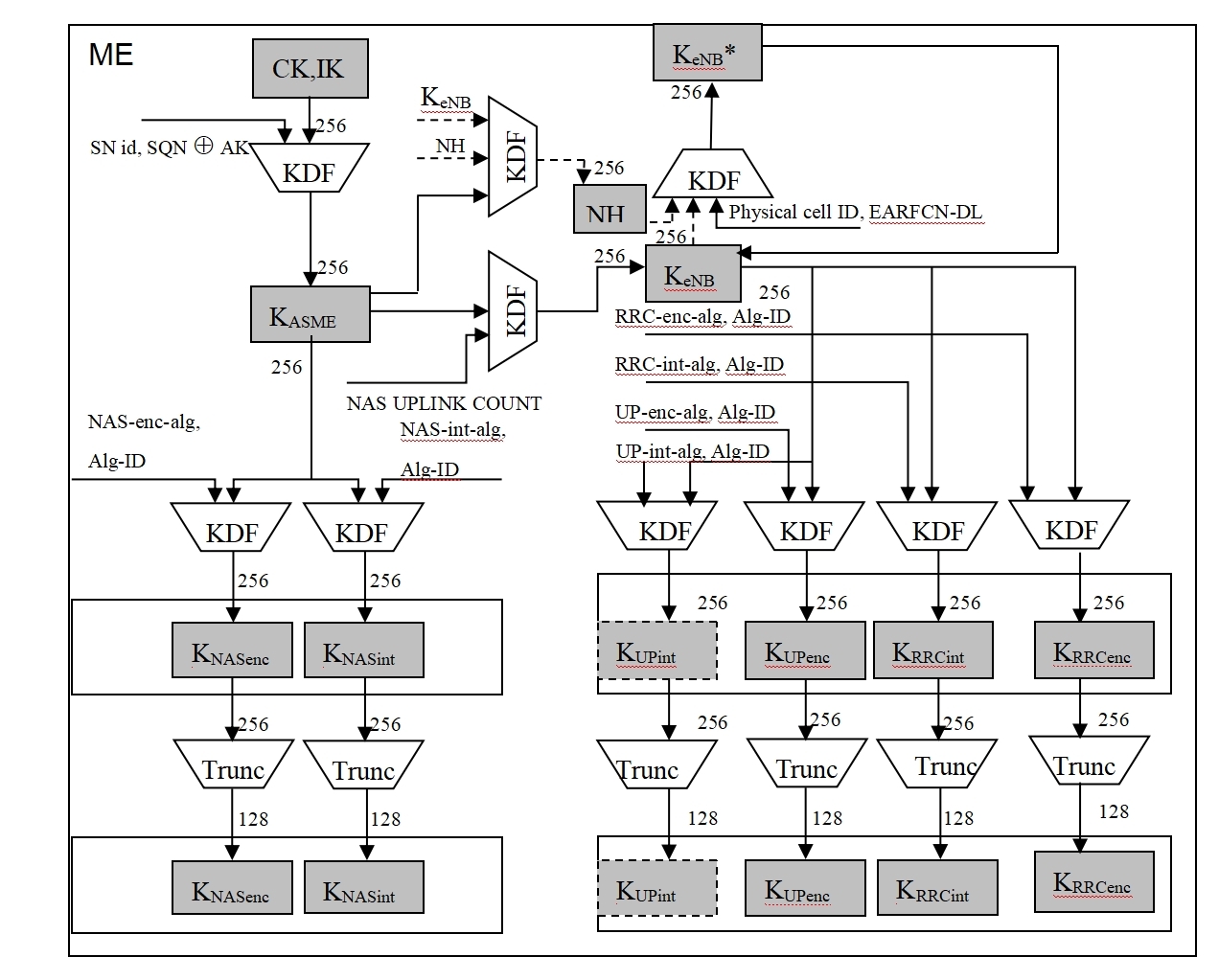
Figure 4: Generation process of terminal authentication parameters
●When the 4g lte wireless data terminal roams, switches or re-accesses between eNodeBs, it can use the re-authentication mechanism to re-authenticate and update keys to ensure security during mobile access.
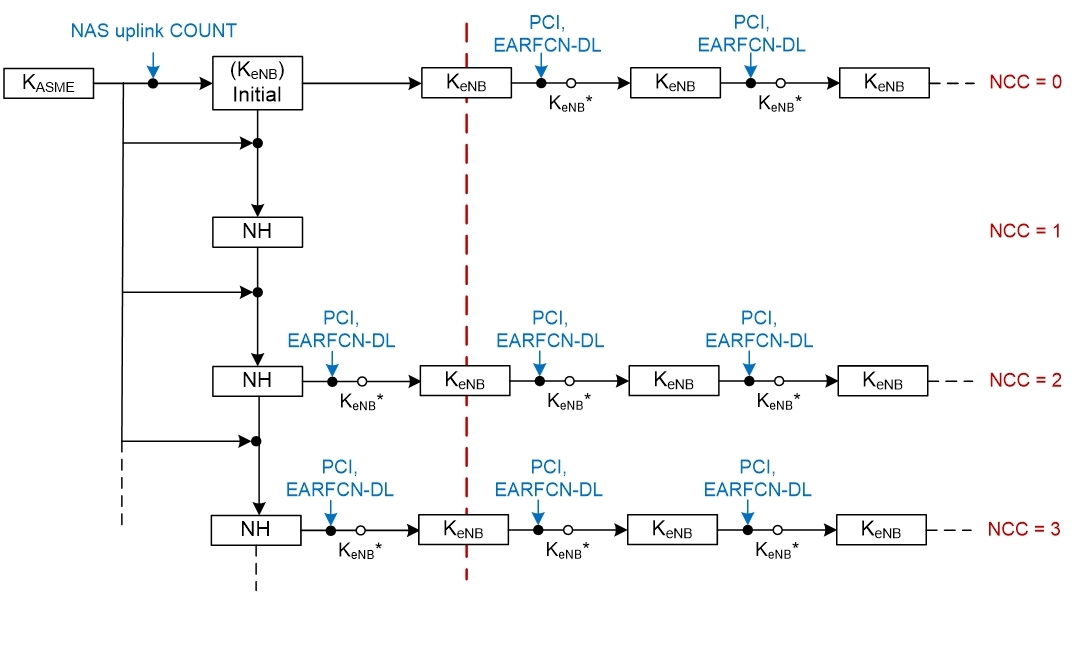
Figure 5: Key handling when switching
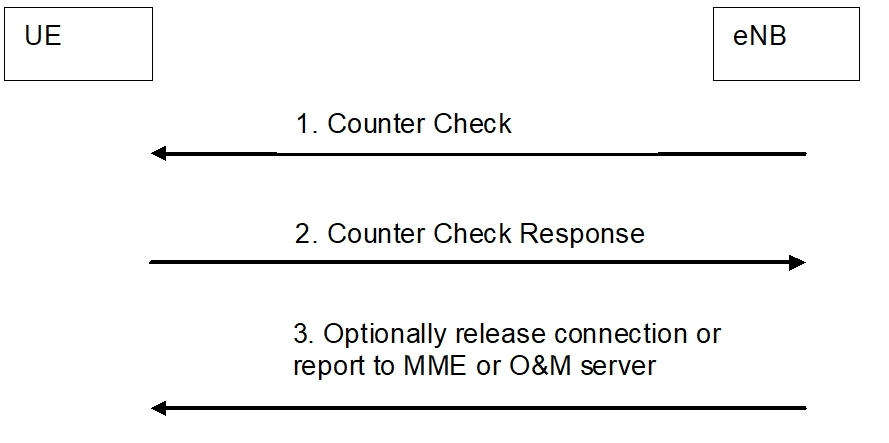
Figure 6: Periodic authentication of terminals by eNB
●Authentication signaling process
Authentication is required when the UE initiates a call, is called, and registers. Encryption/integrity protection may also be performed after authentication is completed. The UE calculates RES (authentication response parameters in the SIM card), CK (encryption key) and IK (integrity protection key) based on the RAND sent by the LTE private network, and writes the new CK and IK into the SIM card. and send the RES back to the LTE private network. If the LTE private network considers that the RES is correct, the authentication process ends. After successful authentication, the LTE private network decides whether to execute the security control process. If yes, it is triggered by the LTE private network, and encryption/integrity protection is implemented by the eNodeB.
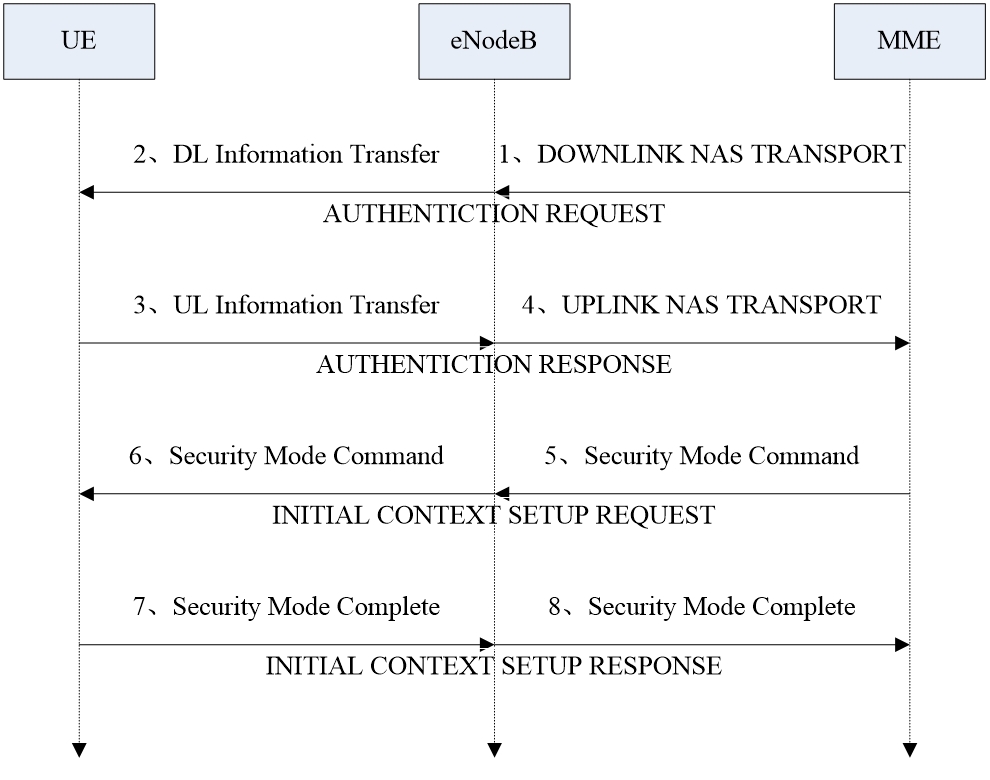
Figure 7: Authentication signaling process
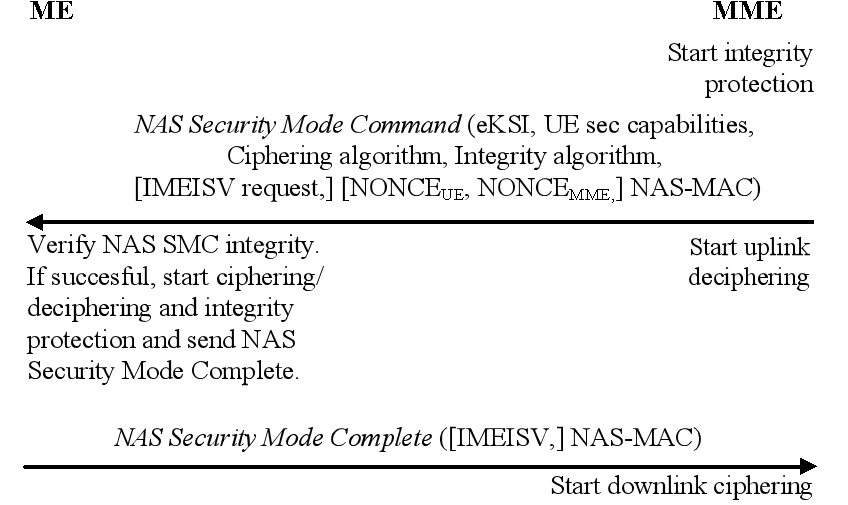
Figure 8: Safe mode signaling process
Application Layer
● When users access, security authentication is implemented at the application layer to prevent illegal user access.
● User data can use the IPSEC mechanism to ensure user data security.
● When a problem is discovered during application, the user with the problem can be forced to go offline by scheduling operations such as forced disconnection and remote killing.
Network Security
● The private network business system can connect to the external network through firewall equipment to ensure that the private network is protected from external attacks. At the same time, the internal topology of the network is shielded and hidden to prevent network exposure and maintain network security.
Post time: Apr-25-2024